
(Image from: Visual China)
The seemingly distant Internet of Things has actually outlined a general outline in our lives. Despite things like “Jarvis†(Iron Man’s smart steward), home living with full control over voice has not gained widespread popularity, but many smart applications have occupied many moments in our lives.
For example, it is not a new skill for auto-reversing and observing the surrounding obstacles for current automobiles; the cost of paying for life online without leaving home, through an intelligent water grid system, has also become an issue. Everyday; In addition to the development of consumer-grade equipment, smart devices are also beginning to find widespread use in industries such as manufacturing, mining, utilities, and agriculture.
However, the problem is that many smart products are very fragile in terms of security. Titanium media reporters at the Safety Geek Carnival called “HACKPWN2016†saw a lot of Chinese geeks and coffee companies crack all kinds of products from various aspects of hard software.
Self-driving cars, from technology vendors to consumers, have placed great expectations on this technology. Autopilot technology requires the use of sensors to sense the surrounding environment, obtain data from ranging, and make path planning based on the surrounding environment and data to form an autonomous driving state. The feedback information can also be displayed on the interface of human-computer interaction, providing the driver with the basis for driving judgment.
The function of the sensor is basically measured by the ultrasonic sensor to measure the short distance. The high-definition camera recognizes the road sign and distance, LiDAR generates a 3D map, and the radar detects the long distance. The idea of ​​cracking is to attack the above sensors, generate the wrong input source, and then affect the driver's judgment.
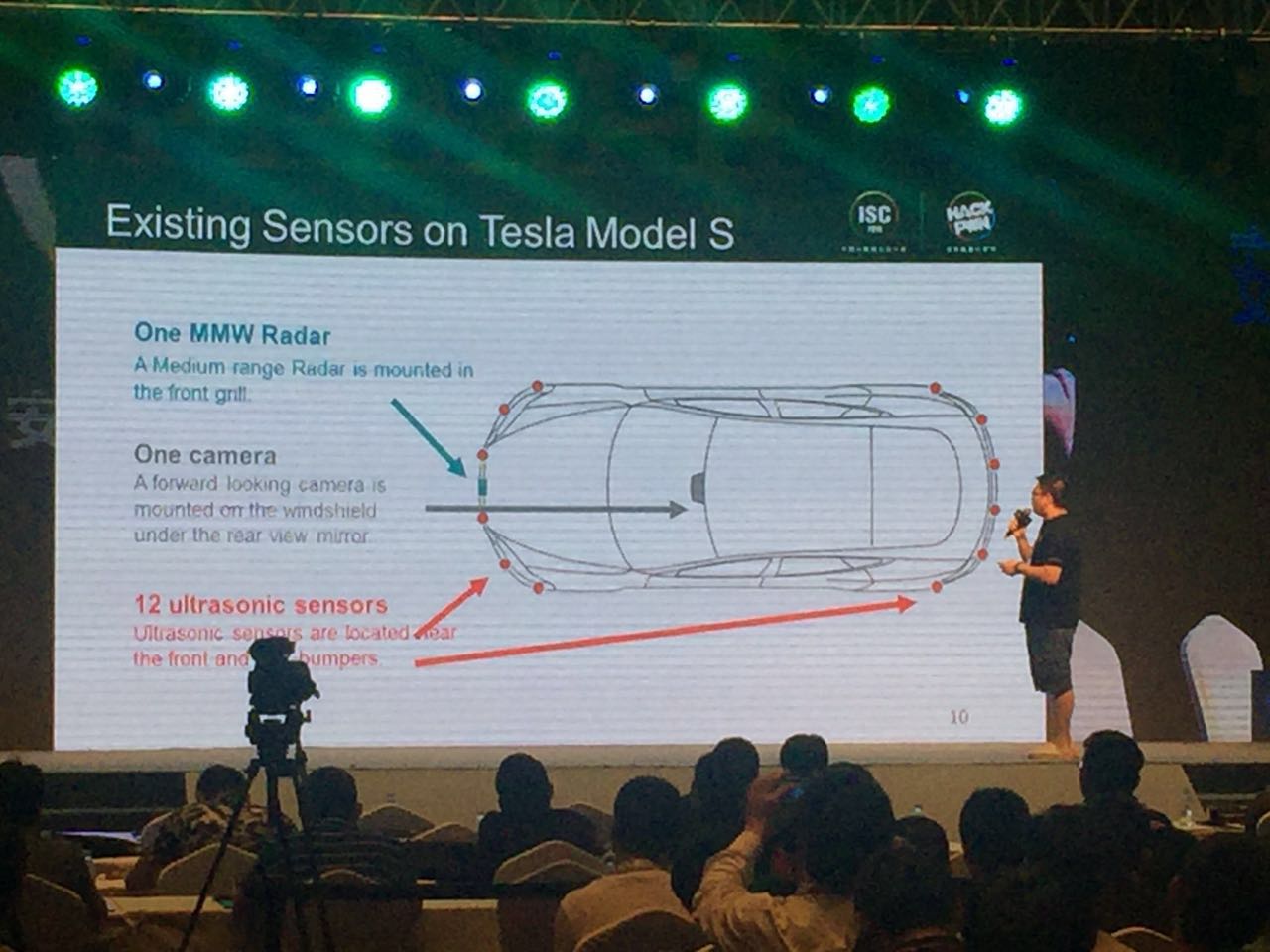
For example, Tesla is composed of a millimeter-wave radar, a high-definition camera, and 12 ultrasonic sensors that make up its perception. In Tesla’s automatic driving accident in the United States, Tesla’s color identification for the white truck was correct, but it was impossible to distinguish it from the road. The radar detection wave also happened to cross this area, causing Tesla to drill directly. To the bottom of the truck.
Not only Tesla, but mainstream cars equipped with sensors in the current market are vulnerable to malicious attacks. Prof. Xu Wenyuan and his team from Zhejiang University have cracked the display of several cars on the market. Titanium media reporters saw in the live demonstration that there are certain loopholes in various parts, such as:
For ultrasonic sensors, interference source equipment is used to hide obstacles, so that the sensor can lose the ability to detect normally, and it can also create illusions of obstacles, so that the car can stop driving at an instant; Some new materials that can be purchased on Taobao can also create stealth effects on sensors. ; Using the interference source method, the millimeter-wave radar can also lose its working effect, and the monitoring of vehicles on the travel path will be deviated; And let the camera lose functionality, only need to be a laser pointer."Speaking so much is not for everyone to buy a self-driving vehicle ," explains Xu Wenyuan . "But when we design autonomous vehicles, especially sensors, designers should consider conscious attacks and consider these scenarios. For us to buy a car, a self-driving vehicle can be bought, but it has not yet reached true automatic driving."
In addition to cars, many of the devices used in high-frequency use scenarios were also easily cracked by geeks and coffee. For example, through the attack transmission protocol, using the parallel permission mechanism to tamper with the robot's response to the problem; using the loopholes of the key generation mechanism to crack the car remote control rolling code; the virus that is implanted in the mobile phone can be seamless and fast on the PC and the mobile terminal. Cross infection; 20 seconds to crack win 10, remote control desktop window......
Data Group IDG once predicted that the Internet of Things market will reach 1.7 trillion in 2020, and the number of terminals connected to the Internet of Things will reach 50 billion; and Gartner expects that the black market for IoT will exceed 50 in 2020. One hundred million U.S. dollars.
The flourishing development of the Internet of Things has also led to the upgrading of the gray industrial market and technology. The lack of common sense in security and the high threshold of self-protection in front of new technologies has made the infringement in the intelligent field even more secretive and immense.
Just think, how many people will carefully review the smart device's claim terms? Or who can perceive that Trojan viruses continue stealing personal information in smart devices? 360 founder CEO Zhou Hongyi also made a speech at this year's cyber security conference. He said, "Being a company for 11 years, the most helpless thing is domestic companies' disregard for cyber security."
When the wheel of science and technology and social progress comes to the threshold of a comprehensive upgrade, the pursuit of a more convenient and more comfortable life is more like a kind of human fate, but the technology itself is a double-edged sword. People will want to discard security while gaining convenience. In an era of over-burdened capital and consumer spending, explicit consumer demand will of course require technological progress to meet, but the implicit requirements in private security must also keep up with the pace of technology.
More cutting-edge technologies, focusing on titanium media micro-signals: Titanium media (ID: taimeiti) 
Titanium Media WeChat QR Code